For those out there that are wondering what CryptoLocker is, or those that have suffered the effects of the CryptoLocker Virus then you’ll be interested to know what it is and how to prevent paying your hard earned cash to get your data back.
What is CryptoLocker:
CryptoLocker surfaced in 2013, a refinement of previously known versions of ransomware, which has affected many users by restricting access by not just locking the system but also encrypting certain files – hence being called as CryptoLocker.
Since the discovery of this malware, the number of its victims has exponentially grown. Trend Micro’s October 2013 report, observed that over a 30-day period that 64% of detected global infections were seen in the US. UK and Canada had their share of infections at 11% and 6%, respectively.
As with any ransomware, once the system is infected, the user is coerced to pay (a ransom) through online payment methods to regain computer usability. However, paying doesn’t guarantee access to the infected system.
How does your system get infected by the Cryptolocker Virus?
The threat starts as a spammed message with a malicious attachment (in this case, detected as TROJ_UPATRE.VNA). Should users open the attachment, TROJ_UPATRE.VNA then downloads and executes cjkienn.exe. The said file is a ZBOT variant detected as TSPY_ZBOT.VNA.
Along with its malicious routines that include stealing online banking credentials, TSPY_ZBOT.VNA also downloads a CryptoLocker variant onto the infected system. This variant, which serves as the final payload, is detected asTROJ_CRILOCK.NS.
What happens once CryptoLocker is executed?
CryptoLocker then searches for files with certain file extensions to encrypt. It then encrypts important productivity documents and files such as .doc, .docx, .xls, .pdf, among others.
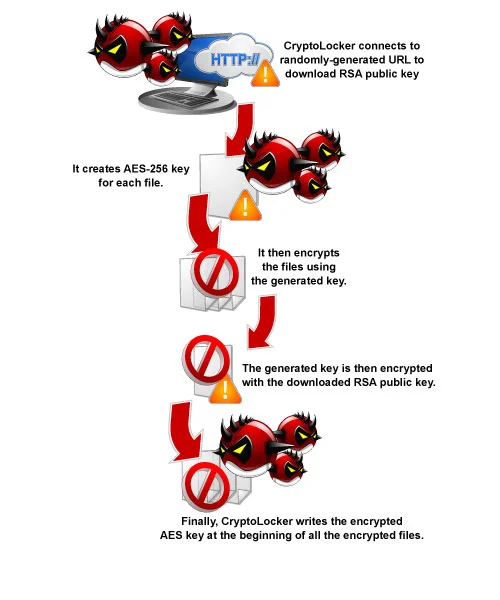
How does the encryption work?
Cryptolocker is notable due to how it encrypts the user’s files – namely, it uses AES-265 and RSA encryption method – in order to ensure that the affected user has no choice but to purchase the private key. The encryption process based on our analysis looks like the following:
The RSA public key can only be decrypted with its corresponding private key. Since the AES key is hidden using RSA encryption and the RSA private key is not available, decrypting the files is not feasible as of this writing.
How to Prevent Becoming a Victim:
- Ensure your operating system and security software are regularly updated.
- Consider investing in substantial anti-virus tools and manage them properly
- Don’t open attachments from unknown sources or from emails that appear to be from a legitimate source but are suspicious.
- Ensure that you have a backup of your Data that is stored independent to your system. Using KEE’s Managed Cloud Backup ensures that you have multiple copies of your data held not only onsite, but offsite in the cloud in-case other systems on the network are effected.
- Ensure that you have multiple generations (Copies) of your data, Our leading technology can entire that an automated schedules are setup to backup your data on a daily basis and offsite multiple generations to our secure Enterprise Cloud.
- Adopt a strategy to identify if a computer is infected (Or let KEE do this for you) and disconnect it from networks immediately and seek professional advice.
- If you believe you have been compromised, change online account passwords and network passwords after removing the system from the network.
- Block .exe files over email, including within ZIP files. This can usually be done using an anti-spam system.
Summary:
Scrutinise email messages carefully. Be wary of every email you receive, specially those from unverified sources. Users can do this by doing their research or communicating directly to the purported sender to confirm if they sent the messages.
Refrain from clicking links embedded in email. It is best to avoid clicking links in email. However if you need to, make sure that your browser uses web reputation to check the link.
Comprehensive Secure Backups. The 3-2-1 rule applies here – three backup copies of your data, on two different media, and one of those copies in a separate location. Cloud storage services can help here.
To ensure that you are not impacted then follow the Checklist above to ensure that your own personal data and your business systems are protected and secure.
For company systems you can ensure that they are operational again in minutes with our Instant Recovery solution, for more information feel free to contact us to discuss options on how to protect your data and ensure that in any scenario, you are able to recover without cost, quickly and easily.